HIPAA Compliance and Your Practice: Part 2 of 3
The entire HIPAA legislation is no quick read! Its length and technical jargon may make it difficult for you to know where and how to start becoming HIPAA compliant.
For healthcare providers wanting to take a step toward having a HIPAA-compliant practice, these basic HIPAA rules are a good place to start: Privacy, Security, and Breach Notification.
It’s also important to keep in mind that these apply to:
- Covered entities. Health plans, healthcare clearinghouses, and healthcare providers that create, maintain, or transmit PHI.
- Business associates. Any entity that is provided with access to PHI in order to perform services for a covered entity.
Privacy, Security, and Breach Notification
Privacy Rule
The HIPAA Privacy Rule largely covers protected health information (PHI). It points out the restrictions and conditions that need to be observed when using and/or disclosing PHI. It discusses what can and cannot be shared without patient authorization, and with whom such information can be disclosed.
The Privacy Rule also gives patients (or their nominated representatives) rights over their PHI. These rights include being able to obtain a copy of and/or examine their health records as well as being able to request necessary corrections.
Under the Privacy Rule, covered entities are strongly advised to:
- Provide HIPAA education and training to employees
- Ensure that appropriate steps are taken to maintain the integrity of patients’ PHI
- Ensure that patients provide written permission before their health information is used for purposes such as marketing, fundraising, or research
Even when the use or disclosure of PHI is permitted under the HIPAA Privacy Rule, it still needs to go through the minimum necessary standard, which means that access to PHI is limited to the minimum amount of information necessary to fulfill the intended purpose of the particular disclosure, request, or use.
Security Rule
The HIPAA Security Rule defines and regulates the standards, methods, and procedures that must be applied to electronically stored, accessed, and transmitted PHI (ePHI).
The Security Rule comprises three parts—technical, physical, and administrative safeguards. Some safeguards must be implemented (required), while some can be implemented with a reasonable amount of flexibility (addressable).
Here they are according to
HIPAA Journal’s Compliance Checklist:
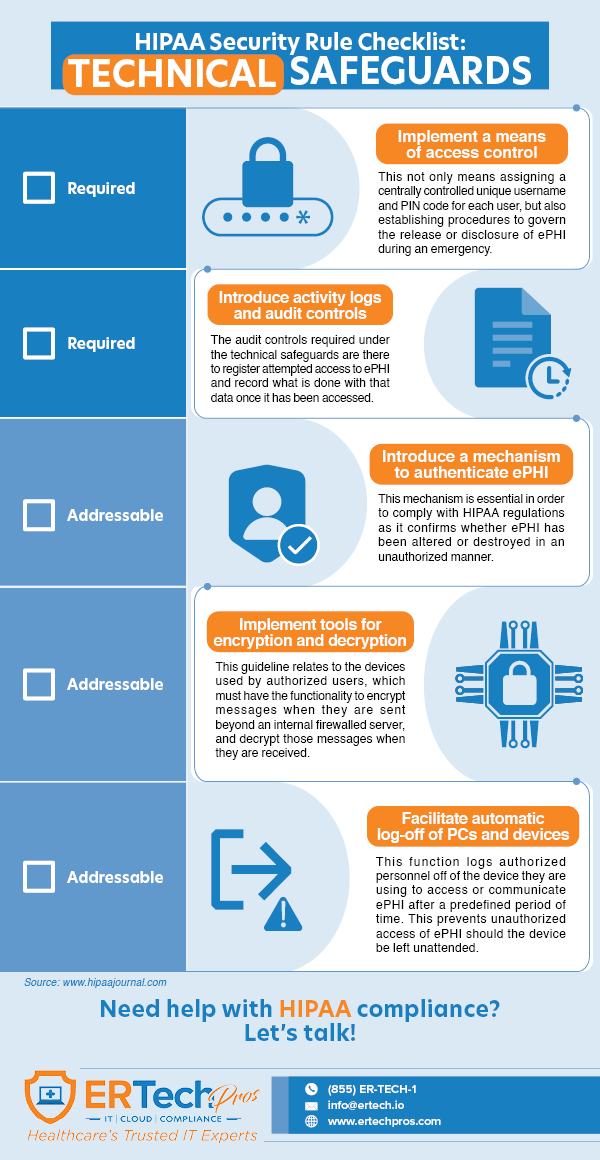
Technical Safeguards
The technical safeguards focus on the technology used to protect and provide access to ePHI. HIPAA requires ePHI (at rest or in transit) to be encrypted according to
NIST standards once ePHI goes beyond an organization's internal firewalled servers.
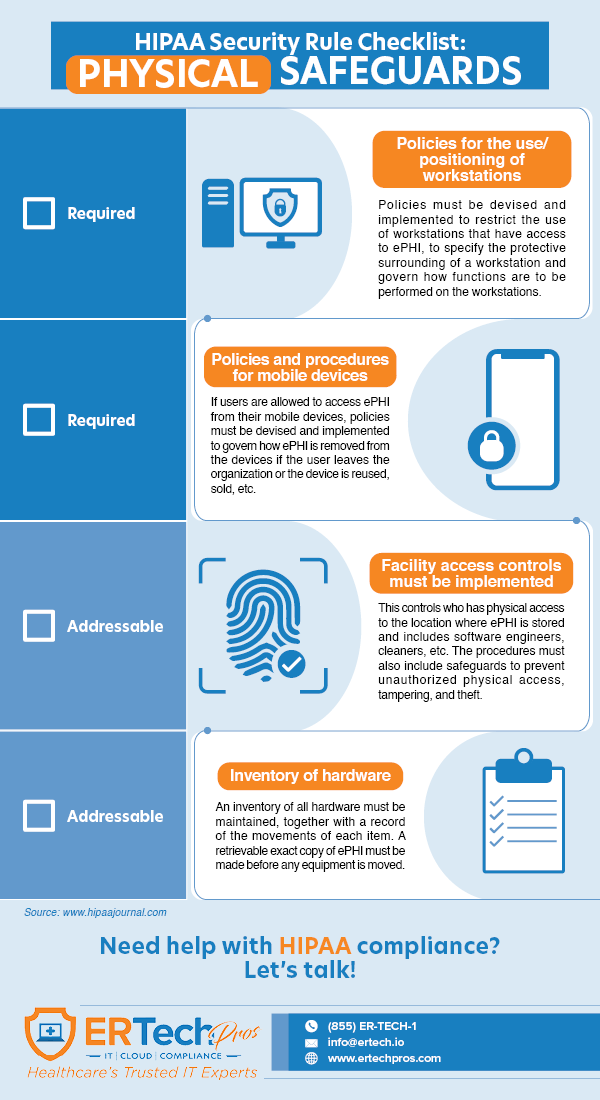
Physical Safeguards
The physical safeguards cover physical access to ePHI, whether these are stored in on-premise servers, on the cloud, or in an offsite data center.
Administrative Safeguards
The administrative safeguards focus on internal organization, workforce management, maintenance of security measures that ensure the protection of ePHI.
Breach Notification Rule
According to the US Department of Health and Human Services (HHS), a breach is generally defined as an impermissible use or disclosure under the HIPAA Privacy Rule that compromises the security or privacy of the PHI.
In the event of a PHI breach, the Breach Notification Rule requires covered entities to provide notifications to certain parties without unreasonable delay and in no case later than 60 days following the incident:
- Affected Individuals. Individual notice must be in written form and sent by first-class mail or, if the affected individual has agreed to receive such notices electronically, via email. The notice must include a brief description of the breach, what types of information were involved in the breach, what the individuals should do to protect themselves from potential harm, and contact information for the covered entity. It should also contain information on what the entity is doing to investigate the breach, mitigate its effects, and prevent any further security incidents.
- Secretary of HHS. If the breach affects 500 or more individuals, a notice must be sent to the Secretary promptly after the incident. However, if a breach affects fewer than 500 individuals, the covered entity may notify the Secretary about such breaches in an annual report.
- Media. If the breach affects more than 500 residents of a state or jurisdiction, covered entities are required to issue a notice to prominent media outlets serving the area. This is typically done in the form of a press release and must include the same information required for the individual notice.
| What happens if you break HIPAA rules? Read HIPAA Compliance and Your Practice: Part 3 of 3
HIPAA Compliance Experts At Your Service
HIPAA compliance deals a lot more than just the basics, which is why you need a reliable partner as you take steps in getting that HIPAA Seal of Compliance for your healthcare practice.
ER Tech Pros is a managed service provider that specializes in giving healthcare practices the IT, cloud, and compliance technology they need to keep their data secure and their operations HIPAA compliant.
If you found the checklists above to be helpful and practical, we’ve got more in store for you!
Search Articles